The Akira Ransomware Saga: Origins, Tactics, and Countermeasures
In the ever-evolving landscape of cybersecurity threats, one name has recently gained notoriety – Akira Ransomware. This malicious software has wreaked havoc on countless individuals, businesses, and organizations, leaving a trail of encrypted data and financial losses in its wake. In this blog post, we will delve into the inner workings of Akira Ransomware, exploring its origins, mode of operation, and the implications it has for cybersecurity.
Unveiling the Origins
In March, the US and Canada were attacked with a new family of ransomware called Akira. It’s not like the Akira ransomware that Microsoft Defender Antivirus flagged in 2017. Several organizations in the US were targeted and their sensitive data was exposed by the ransomware.
Akira Ransomware first made its appearance in the cyber threat landscape in March 2023. The threat actors behind Akira employ various extortion strategies, operating a website on the TOR network (with a .onion domain). This site lists victims and any stolen information, especially if the ransom demands aren’t met. Victims are directed to this TOR-based site, using a unique identifier found in the ransom message they receive, to initiate negotiations.
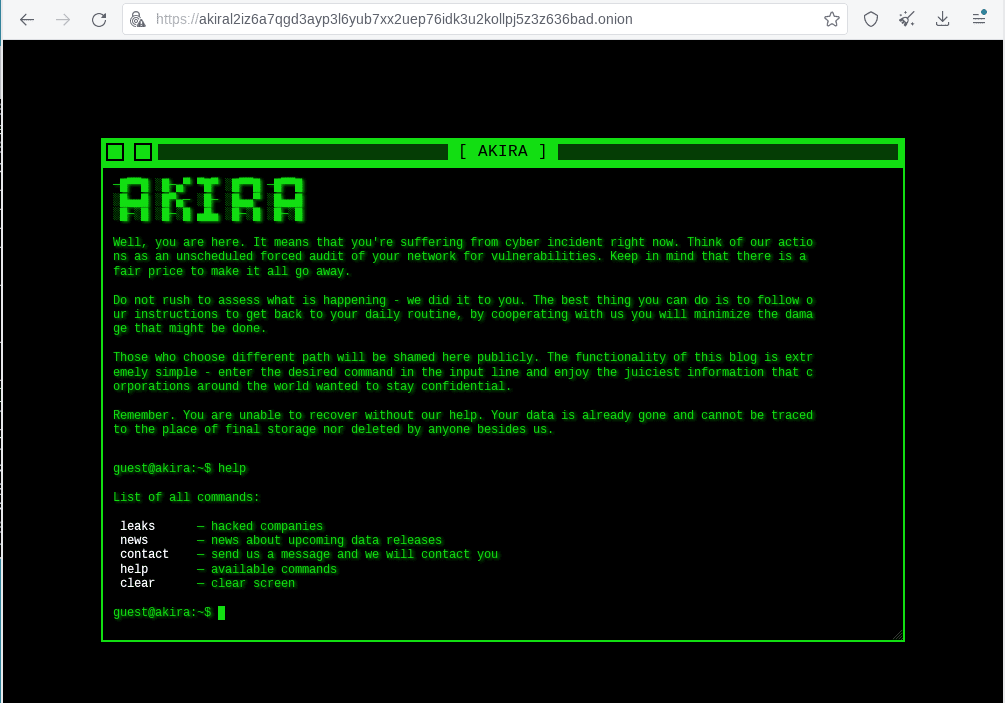
Changes Noticed in the 2023 Version
Targeting VPNs Lacking Multi-Factor Authentication (MFA):
Threat actors started targeting Cisco VPNs that weren’t configured for multi-factor authentication in 2023. By using this tactic, they could infiltrate organizations more easily. By implementing MFA, you’ll be able to reduce the risk of unauthorized access, including ransomware infections. In the event that a threat actor gets unauthorized access to VPN credentials, MFA provides an extra layer of protection.
Advanced Attack Techniques:
Attackers target VPNs by exploiting exposed services or applications. Their focus is on MFA vulnerabilities and VPN software vulnerabilities. In order to get a foothold in a target network, they use LSASS dumps (Local Security Authority Subsystem Service) to extract credentials and escalate privileges. In addition, the group has been linked to using tools like PCHunter64 and creating minidumps to gather more information.
Brute-Forcing vs. Purchasing Credentials:
- Brute-Force: Evidence suggests the attackers used brute force and password spraying. The brute force method involves trying various combinations of usernames and passwords until the right one is found. An attacker tries a few common passwords against lots of usernames in password spraying.
- Purchasing Credentials through Dark Web Market: Attackers can sometimes acquire valid credentials by purchasing them on the dark web. Data breaches or other means might have made these credentials available. As the attacker would simply log in using valid credentials, this method would leave no trace in the VPN’s logs.
Detection from Cisco Logs:
- Login attempts with invalid username/password (%ASA-6-113015)
Example:
%ASA-6-113015: AAA user authentication Rejected: reason = reason : local database: user = user: user IP = xxx.xxx.xxx.xxx - Remote access VPN session creation attempts for unexpected connection profiles/tunnel groups (%ASA-4-113019, %ASA-4-722041, or %ASA-7-734003)
Ransomware Analysis:
The Akira Ransomware sample, identified by its SHA256 hash 3c92bfc71004340ebc00146ced294bc94f49f6a5e212016ac05e7d10fcb3312c, is a console-based 64-bit executable crafted using the Microsoft Visual C/C++ compiler.
The ransomware starts its operation by using the GetLogicalDriveStrings() API function to enumerate and get a list of all logical drives in the system when it’s executed. As a result, Akira drops his ransom note across multiple folders under the name “akira_readme.txt”. During its malicious activities, the ransomware scans for files and directories to encrypt. The API functions FindFirstFileW() and FindNextFileW() facilitate this encryption process. The Akira software excludes certain file extensions and names during its encryption phase, so .exe, .dll, .sys, .msi, .lnk, and .akira files aren’t affected.
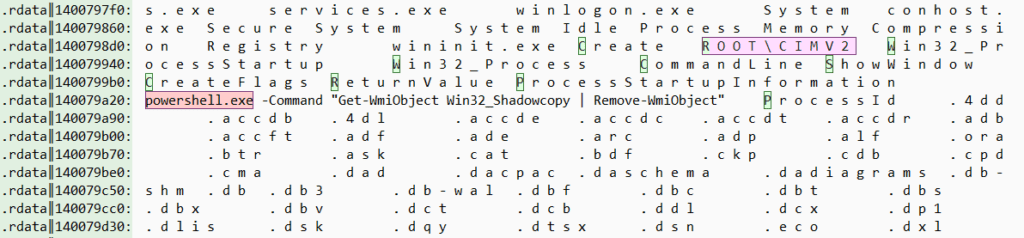
The presence of the command powershell.exe -Command Get-WmiObject Win32_Shadowcopy | Remove-WmiObject within the strings extracted from Akira Ransomware’s static analysis is particularly concerning. This command is a clear indication of the ransomware’s intent to hamper recovery efforts. Specifically, the command utilizes PowerShell to interact with the Windows Management Instrumentation (WMI) system, targeting the Win32_Shadowcopy class. The Win32_Shadowcopy class represents the shadow copies on a system, which are essentially backup copies or snapshots of computer files or volumes. By piping (|) the results of the Get-WmiObject Win32_Shadowcopy command to Remove-WmiObject, the ransomware instructs the system to delete all existing shadow copies. This action effectively prevents victims from restoring their files to a previous state using Windows’ native shadow copy functionality. By eliminating this potential recovery method, Akira Ransomware further pressures its victims into paying the ransom, as traditional backup restoration options become limited or non-existent.
Akira ransomware employs a sophisticated encryption mechanism, leveraging the “Microsoft Enhanced RSA and AES Cryptographic Provider” libraries. Drawing from the CryptoAPI, it utilizes functions such as CryptAcquireContextW(), CryptImportPublicKeyInfo(), CryptGenRandom(), and CryptEncrypt(). Notably, Akira combines the robustness of both RSA and AES encryption algorithms and is equipped with a hardcoded base64 encoded public key. Upon successful encryption, it appends a distinctive .akira extension to the filenames, signaling the completion of its encryption process.
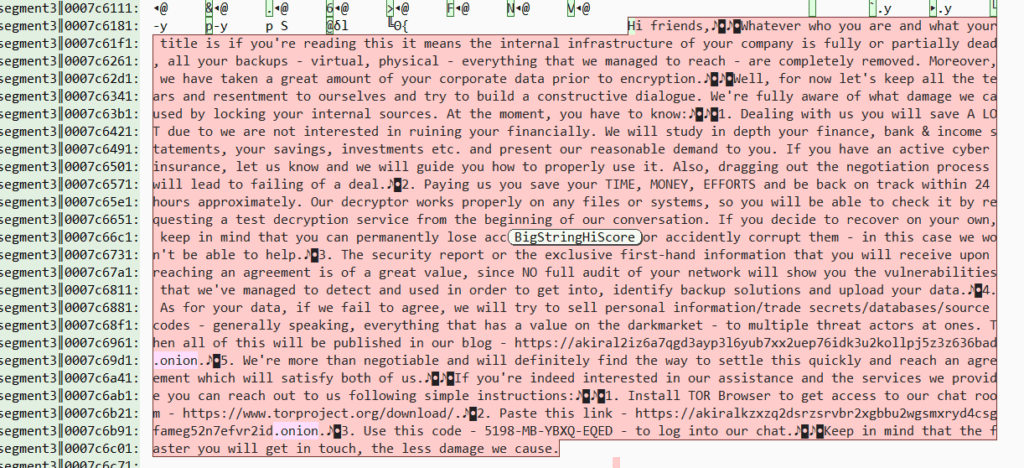
Upon infection by Akira ransomware, victims receive a “akira_readme.txt” note. This message details the compromise of their system, warns of data exfiltration, and demands a ransom. To negotiate, victims are directed to a specific chat room on the dark web via a provided Tor link. The attackers emphasize the risks of non-compliance, including potential data sale on the dark market.
TOR Link:
hxxps://akiral2iz6a7qgd3ayp3l6yub7xx2uep76idk3u2kollpj5z3z636bad[.]onion/
Public Key
-----BEGIN PUBLIC KEY-----
MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAlGDrPaVAQy+cIqMWA2v2
M7ntzniNYnp1hvAuxCOgTpTUN+Z2TwAR4pt2YdQD2As5e/rWgZlqsi/d31OzMSWo
FtliVyiSBuTtnJuoTRjGlUAazvi1PCVbckWVsZO7YDevn8lZ2ouzCRTF7X+AKyQZ
dpHLTfDBY/AXBkZ8BGYJjFu3kVhRQZL47VjGoQvzBi7JCCJyVfxN+KUjQtKmuxuQ
jDqZcqkzcppcqRXIDVm7YuogSgrcNBbdo6PBTzE0I/Cd7P/xCe5eO5ejIPtMg6I3
wHcIIMf5sa7h+TskS093kRVEgj3FWO1KeZBA2Ep4qM8kOw2/uN+idjOVKpLcN1zO
WkTXEQMIPkt9gYtItAb3VofqGhBXmM95SCRYqAagaPQXKTU2oXM5z9YvgYmG5Enb
TAymgAkC/u6ckAmlODH0FOsm1be9ygcTGaTuZQXQ0oQY1UvIs5kciA+wrMdmw07m
cvqj/Lto3fi447RqeZjkOqFQZREok+a2Wjk28FYbWKm4AWEOFNx2gAjdlXPCZr8x
sDlAVQ4arDhjon7j4ink1HS5Ybh+RcgvJpQgQ6QyplI4lT3YGXzE/hQnAuqeXzI3
ORtGLvbJ1X29buoFIFQhc/48Rm96hHYGDrr8qDkVXCDdK2ebV89ODbgIaEQSZrql
HA2I94pqZC43Ps8yYmBMBkcCAwEAAQ==
-----END PUBLIC KEY-----
Akira Ransomware: Key Services in its Crosshairs
.abcddb, .abs, .abx, .accdb, .accdc, .accde, .accdr, .accdt, .accdw, .accft, .adb, .ade, .adf, .adn, .adp, .alf, .arc, .ask, .avdx, .avhd, .bdf, .bin, .btr, .cat, .cdb, .ckp, .cma, .cpd, .dacpac, .dad, .dadiagrams, .daschema, .db-shm, .db-wal, .dbc, .dbf, .dbs, .dbt, .dbv, .dbx, .dcb, .dct, .dcx, .ddl, .dlis, .dqy, .dsk, .dsn, .dtsx, .dxl, .eco, .ecx, .edb, .epim, .exb, .fcd, .fdb, .fic, .fmp, .fmp12, .fmpsl, .fol, .fpt, .frm, .gdb, .grdb, .gwi, .hdb, .his, .hjt, .icg, .icr, .idb, .ihx, .iso, .itdb, .itw, .jet, .jtx, .kdb, .kdb, .kexi, .kexic, .kexis, .lgc, .lut, .lwx, .maf, .maq, .mar, .mas, .mav, .maw, .mdb, .mdf, .mdn, .mdt, .mpd, .mrg, .mud, .mwb, .myd, .ndf, .nnt, .nrmlib, .nsf, .nvram, .nwdb, .nyf, .odb, .oqy, .ora, .orx, .owc, .pan, .pdb, .pdm, .pnz, .pvm, .qcow2, .qry, .qvd, .raw, .rbf, .rctd, .rod, .rodx, .rpd, .rsd, .sas7bdat, .sbf, .scx, .sdb, .sdc, .sdf, .sis, .spq, .sql, .sqlite, .sqlite3, .sqlitedb, .subvol, .temx, .tmd, .tps, .trc, .trm, .udb, .udl, .usr, .vdi, .vhd, .vhdx, .vis, .vmcx, .vmdk, .vmem, .vmrs, .vmsd, .vmsn, .vmx, .vpd, .vsv, .vvv, .wdb, .wmdb, .wrk, .xdb, .xld, .xmlff
Akira ransomware casts a wide net, targeting an extensive array of file extensions. From common database formats like .mdb, .accdb, and .sql to virtual machine-related files such as .vmdk, .vhdx, and .vmx. Its reach also extends to specialized data storage formats like .nsf, .sas7bdat, and .xmlff. This vast spectrum of targeted extensions underscores Akira’s intent to cripple essential data repositories and virtual environments, amplifying its impact on victims.
Detecting Akira Ransomware via SIEM (Security Information and Event Management)
SIEM platforms play a pivotal role in identifying and mitigating threats like the Akira ransomware. By analyzing logs and events from various sources, SIEM can pinpoint suspicious activities indicative of a ransomware attack. Here are some potential detection strategies for Akira using SIEM:
Unusual Process Execution
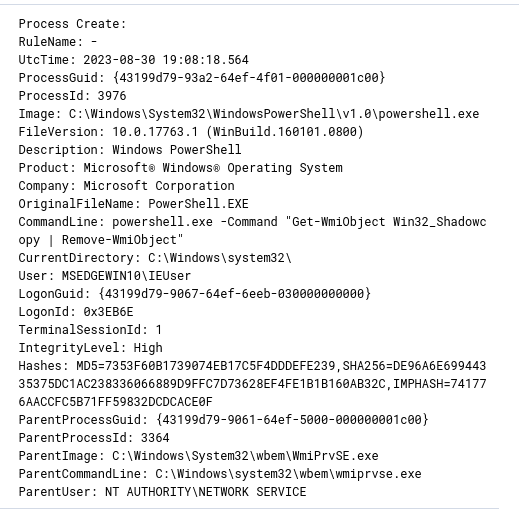
Red Flags in the Registry: Detecting Dubious Entries
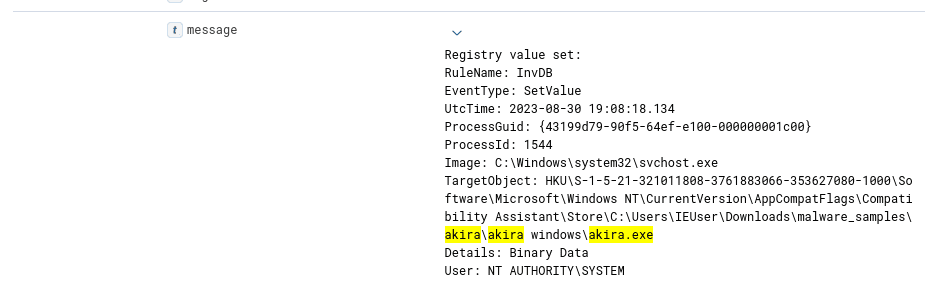
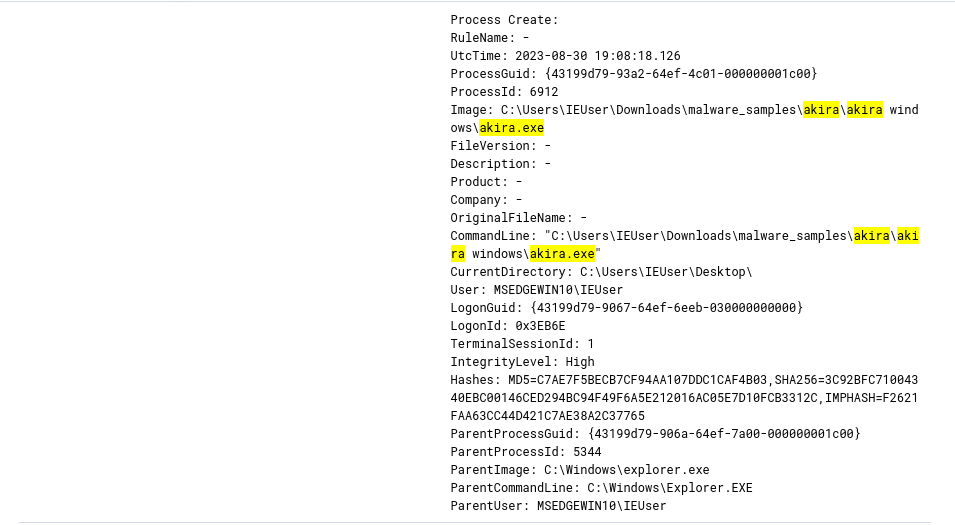
Spotting Stealth: Monitoring Unsigned Binary Executions
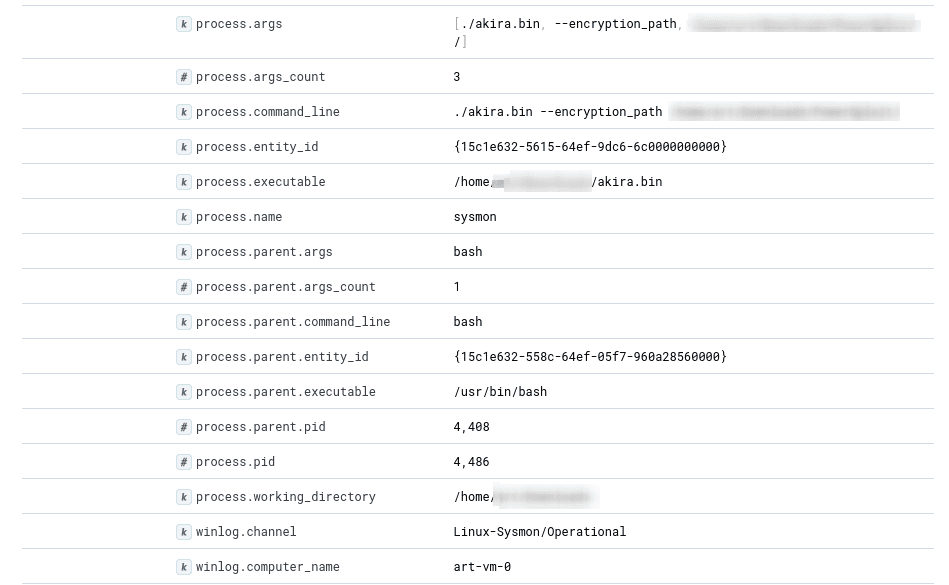
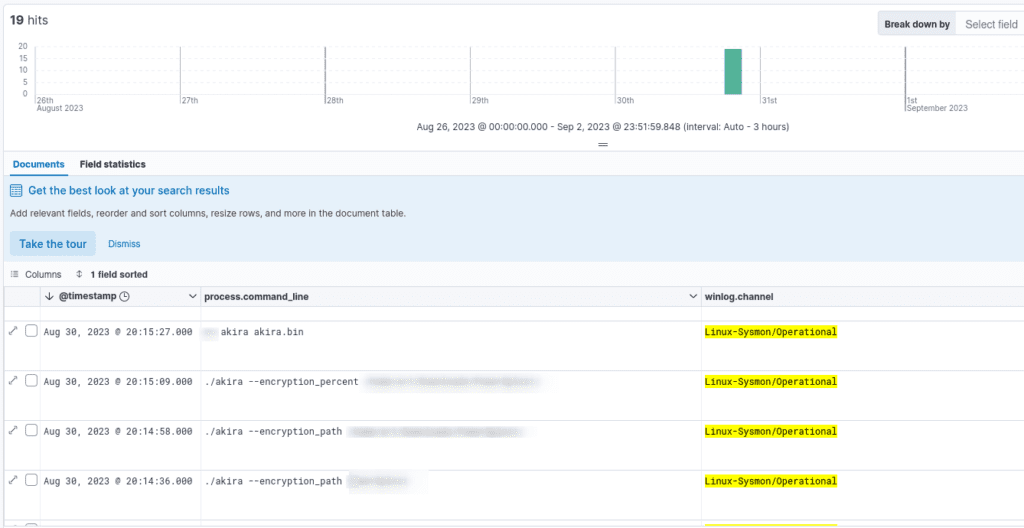
Linux Sysmon Unveiled: Tracking System Activities with Precision
Crafting the Sentinel: YARA Rules for Akira Detection
/*
Akira ransomware
*/
rule Akira
{
meta:
author = "rivitna"
family = "ransomware.akira.windows"
description = "Akira ransomware Windows payload"
severity = 10
score = 100
strings:
$s0 = "\x00--encryption_path\x00" ascii
$s1 = "\x00--share_file\x00" ascii
$s2 = "\x00--encryption_percent\x00" ascii
$s3 = "\x00-fork\x00" ascii
$s4 = "\x00Failed to read share files\x00" ascii
$s5 = ":\\akira\\asio\\include\\" ascii
$s6 = "\x00write_encrypt_info error: \x00" ascii
$s7 = "\x00encrypt_part error: \x00" ascii
$s8 = "\x00Detected number of cpus = \x00" ascii
$s9 = "\x00No path to encrypt\x00" ascii
$s10 = "Paste this link - https://akira" ascii
$s11 = "-----BEGIN PUBLIC KEY-----\nMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA" ascii
$s12 = "\x00Trend Micro\x00" wide
$s13 = " :Failed to make full encrypt\x00" wide
$s14 = " :Failed to make spot encrypt\x00" wide
$s15 = " :Failed to make part encrypt\x00" wide
$s16 = " :Failed to write header\x00" wide
$s17 = " :file rename failed. System error: \x00" wide
$h0 = { 41 BA 05 00 00 00 41 80 FB 32 44 0F 42 D0 33 D2 48 8B C?
49 F7 F2 4C 8B C8 B9 02 00 00 00 41 B8 04 00 00 00
41 80 FB 32 44 0F 42 C1 41 8B C8 48 0F AF C8 48 2B F9 33 D2
48 8B C7 49 F7 F2 }
$h1 = { C7 45 ?? 03 00 00 00 80 7D ?? 31 76 07 C7 45 ?? 05 00 00 00
0F B6 45 ?? 48 0F AF 45 ?? 48 C1 E8 02
48 B? C3 F5 28 5C 8F C2 F5 28 48 F7 E? 48 89 ?? 48 C1 E8 02 }
condition:
(((uint16(0) == 0x5A4D) and (uint32(uint32(0x3C)) == 0x00004550)) or
(uint32(0) == 0x464C457F)) and
(
(7 of ($s*)) or
(1 of ($h*))
)
}
Indicators Of Compromise:
v1 (Windows)
3c92bfc71004340ebc00146ced294bc94f49f6a5e212016ac05e7d10fcb3312c
7b295a10d54c870d59fab3a83a8b983282f6250a0be9df581334eb93d53f3488
678ec8734367c7547794a604cc65e74a0f42320d85a6dce20c214e3b4536bb33
67afa125bf8812cd943abed2ed56ed6e07853600ad609b40bdf9ad4141e612b4
8631ac37f605daacf47095955837ec5abbd5e98c540ffd58bb9bf873b1685a50
1b6af2fbbc636180dd7bae825486ccc45e42aefbb304d5f83fafca4d637c13cc
2084ab8f92a86a37a35879378610949e21ea7b5030313655bb82fe6c67772b0d
4aaa583a9c554ea8e73d4dee0d53eb12dda17df16388f96c0f6ddbaafbcda813
920384692233578a59fc8de2b0205fd9fb20bb0d75c1d5a1534377abf0fc08bc
2b28270c1675990a2c78b31faab547fb75948dd1c2b22e892377ee5e40abebc2
4839fd081e720d7d5091274470679c120378196e1f4faf80c4bac08d8ee7bb8c
9ca333b2e88ab35f608e447b0e3b821a6e04c4b0c76545177890fb16adcab163
d0510e1d89640c9650782e882fe3b9afba00303b126ec38fdc5f1c1484341959
473326da3fff09ee3e486f5f39c090690437ac8bf8bdce556c8033e8f0d730fc
6cadab96185dbe6f3a7b95cf2f97d6ac395785607baa6ed7bf363deeb59cc360
337d21f964091417f22f35aee35e31d94fc3f35179c36c0304eef6e4ae983292
772eb611c9ca20b461536fd0bd87d553dcecf3f4c82e26c2378cad40bbf4b0b0
b3f473b0fd752fcd8b0d5983366c4ccccdacdceb8d6ba25fcb02b34c622cca78
cfbcea795524c69a6d28fd9e60e07437d8f2abd23812109430ca2efd46606310
v2 (Windows)
2e2ad6392e75d5a5155498c2a76cb373d17ca3ad4ba57c6d33c623fca5e29342
3f4ceeada7ff021c30df1646437d2ab0e55997bbb281444501f6d1f4ea8fa209
4cb8365b18b1c319d374be0b9d219144c20fb8714e9cf346e655f854d2c60170
637e28b38086ff9efd1606805ff57aaf6cdec4537378f019d6070a5efdc9c983
92072945358b605c024b9e3335fb33b82faf33048c56f5529aaf5af4bf0c1b30
c239dadd55b55b817fda5b0c2bb062adf399a5b78a8b3280a473d3ae66f81777
fb2433beb961839b36198e242d0dedb7fa85ab3e08a1141d02874aa4235ac776
2a9257c6c74e37d051f78ed5abaa620b71b27fa3604798af077256a128d911bb
89f5f29cf6b5bcfc85b506fb916da66cb7fd398cf6011d58e9409c7813e1a6f3
8738ba49fcd520789569aea7bf7af890741a745c79ae2bef49b93fb46c076c2b
27009c0abd2709cd5cac4c0135b8f3bed3229b0921601638ba9e90713ede91ea
v3 (megazord) (Windows)
c9c94ac5e1991a7db42c7973e328fceeb6f163d9f644031bdfd4123c7b3898b0
Linux
1d3b5c650533d13c81e325972a912e3ff8776e36e18bca966dae50735f8ab296
Proactive measures against Akira ransomware
- Keep an eye out for suspicious email attachments and links. Check the sender’s legitimacy before you open anything.
- Make sure you only download files and programs from trusted stores and official websites. Click away from dubious sites.
- Regular updates: Make sure all your software is up to date. Patching vulnerabilities helps stop cybercriminals from exploiting them.
- Enable multi-factor authentication (MFA) wherever possible and implement strong password policies. It adds another layer of security.
- Keep your critical data backed up offline regularly. Updating these backups will provide a fallback in case of a ransomware attack.
- Report Suspicious Activities: If you suspect ransomware or become a victim of it, report it to the appropriate authorities. It can help track cybercrime activity and perhaps prosecute the criminals.
- Train and Educate: Make sure your employees and users are up-to-date on the latest ransomware threats.
Reference:
https://blogs.cisco.com/security/akira-ransomware-targeting-vpns-without-multi-factor-authentication
https://www.pcrisk.com/removal-guides/26677-akira-ransomware
Conclusion:
Thank you for taking the time to read this article. We hope it provided valuable insights and actionable recommendations to safeguard against the Akira ransomware threat. Knowledge is a powerful tool in the fight against cyber threats, and sharing this information can make a difference. If you found this article helpful, please consider sharing it with your friends, colleagues, and loved ones. Together, we can build a more informed and secure digital community. Stay safe and vigilant!