Phishing Attacks Exploit CapCut’s Popularity to Distribute Multiple Stealers
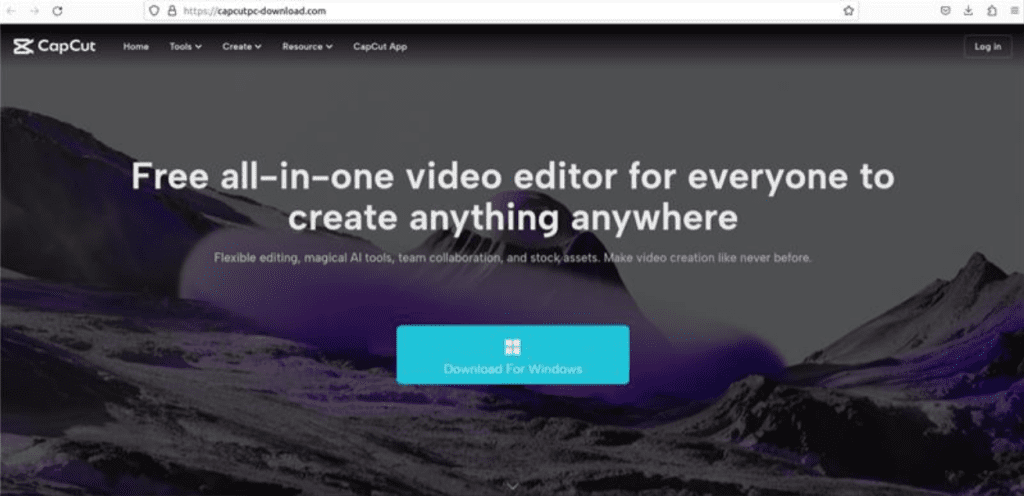
A phishing website posing as video editing software was discovered recently by Cyble Research and Intelligence Labs (CRIL). The fraudulent websites lure users into downloading and executing various types of malware, such as stealers, RATs, etc. This campaign targeted the CapCut video editing tool, a product of ByteDance, the same parent company that owns TikTok.
TAs have been attracted to the application by its increasing popularity in countries around the world over the past few years. Moreover, users might actively seek alternative means to download CapCut due to the ban imposed by Taiwan, India, and several other countries, unknowingly exposing themselves to these malicious websites.
The CapCut phishing website has been used by several TAs to distribute various malware families. In one campaign, a phishing website hosted the Offx stealer, while in another, it hosted BatLoader, which delivered the Redline stealer to targets.
Technical research:
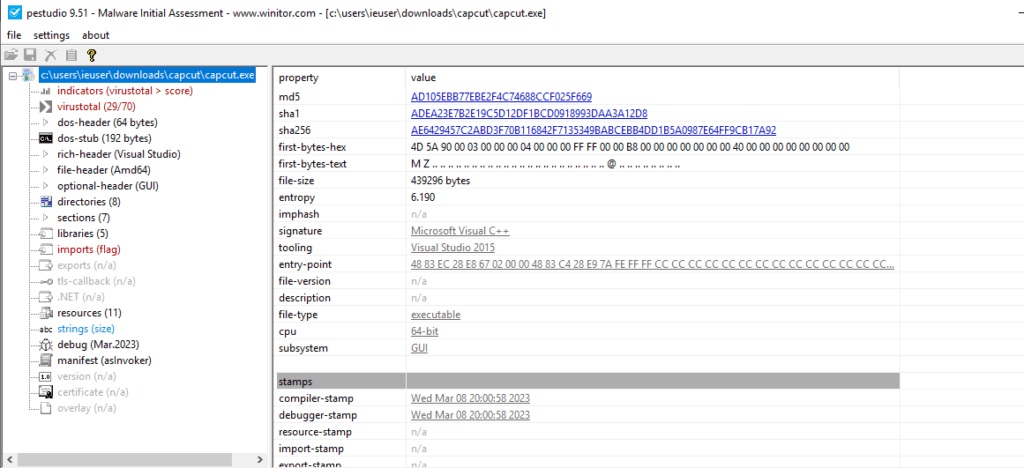
This file, weighing 439,296 bytes, was created using Microsoft Visual C++ and the Visual Studio 2015 tooling. It appears to be specifically designed for 64-bit systems and operates within a graphical user interface (GUI) environment.
While details about the file’s version and description are not available, its signature indicates a connection to Microsoft Visual C++. Furthermore, it seems to be associated with the Microsoft Office manifest, suggesting a potential link to the widely used productivity suite.
Unfortunately, we lack specific information about the file’s import, export, and debug stamps. However, what we do know is that the file exhibits a medium entropy level of 6.190, indicating a moderate level of complexity and randomness. This, coupled with the fact that it is identified as malware, raises serious concerns about its purpose and potential impact on systems.
It’s important to note that this file lacks a digital certificate, and there is no information regarding its validity period. These factors, combined with its malicious nature.
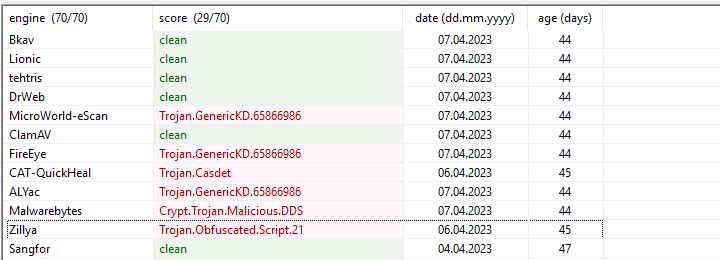
MicroWorld-eScan detects it as Trojan.GenericKD.65866986, with a detection date of 07.04.2023 and a threat level of 44. ClamAV, on the other hand, marks it as clean with the same detection date and threat level. FireEye aligns with MicroWorld-eScan, identifying it as Trojan.GenericKD.65866986 on 07.04.2023 with a threat level of 44.
Moving on, CAT-QuickHeal labels it as Trojan.Casdet, detected slightly earlier on 06.04.2023, and assigns a threat level of 45. ALYac’s findings mirror those of MicroWorld-eScan and FireEye, classifying it as Trojan.GenericKD.65866986 with a threat level of 44 on 07.04.2023. Malwarebytes identifies the file as Crypt.Trojan.Malicious.DDS, also on 07.04.2023, and assigns a threat level of 44. Lastly, Zillya categorizes it as Trojan.Obfuscated.Script.21, detected on 06.04.2023, and assigns a threat level of 45.
Techniques Discovered:
SetWindowLongPtrW:
This function, found in USER32.dll, is associated with Windows operations. It is commonly used for process injection, a technique referred to as T1055. Process injection involves injecting malicious code into a legitimate process, often to evade detection or gain elevated privileges.
GetWindowLongPtrW:
Similar to SetWindowLongPtrW, this function in USER32.dll is also related to Windows operations and process injection (T1055). It retrieves information about the specified window or sets specific attributes of the window.
SendMessageW:
The SendMessageW function in USER32.dll is another technique associated with process injection (T1055). It allows inter-process communication by sending a message to a window or control in another process, potentially facilitating the execution of malicious code.
OpenProcessToken:
This function in ADVAPI32.dll is associated with access token manipulation, a technique known as T1134. By opening the access token of a process, an attacker can modify token privileges, impersonate other users, or escalate privileges within the system.
GetTokenInformation:
GetTokenInformation, also found in ADVAPI32.dll, is another technique related to access token manipulation (T1134). It retrieves information about a token object, such as its group membership, privileges, and user identity, which can be exploited for unauthorized actions.
ConvertStringSecurityDescriptorToSecurityDescriptorW:
This function in ADVAPI32.dll is associated with access token manipulation (T1134). It converts a string-format security descriptor into a valid security descriptor, which can be used for modifying security settings or access controls.
Process Injection
The analyzed file appears to have functionality aimed at detecting injection methods. The following calls were found within the code:
- IsProcessorFeaturePresent (address: 0x14002a1e8): This call is typically used to check for specific processor features or capabilities. In the context of injection detection, it may be employed to identify certain CPU features that indicate the presence of a virtualized or emulated environment, which could suggest the presence of a debugger or sandbox.
- QueryPerformanceCounter (address: 0x14002a1f0): QueryPerformanceCounter is a function used to obtain high-resolution timing information. In the context of injection detection, it could be utilized to measure the time taken by specific operations or code sections. Deviations in the timing could indicate the presence of code injection or debugging activities.
- IsDebuggerPresent (address: 0x14002a218): IsDebuggerPresent is a function commonly used to check if a debugger is attached to the running process. In the case of injection detection, it may be employed to determine if a debugger is present, which could indicate that the file is being analyzed or monitored.
The file includes detection mechanisms to identify injection techniques and detect debugging or analysis tools. These features help the malware evade analysis, hinder reverse engineering, and adapt to security measures. It’s a sneaky tactic used by the malware to hide its true intentions and make it challenging for security experts to uncover its malicious behavior. Stay vigilant and keep your system protected by staying up to date with antivirus software and being cautious about the files you download and execute.
Indicator Of Compromise:
| Indicator | Type | Description |
|---|---|---|
| 8dd5d02bb6313997fcaa6515ccb2308c37a81374baef188554ba20d23602c01c | Sha256 | Offx Stealer |
| 558d420e943e28399915ff504be8b188b7445296 | Sha1 | Offx Stealer |
| fc959c2a5b46b1b51003c688cdc384fa | Md5 | Offx Stealer |
| e9e17c06b5fb1dd95e9622703f8ea55be67ceb6435e7aba688784a854c85aef2 | Sha256 | Offx Stealer |
| b8725a0c47ac37475134996bb1711f61ce73279e | Sha1 | Offx Stealer |
| 7876ff8df973e126f512169fb021c85a | Md5 | Offx Stealer |
| capcut-freedownload[.]com | Domain | Phishing websites |
| capcutfreedownload[.]com | Domain | Phishing websites |
| capcut-editor-video[.]com | Domain | Phishing websites |
| capcutdownload[.]com | Domain | Phishing websites |
| capcutpc-download[.]com | Domain | Phishing websites |
| 3eb99ff875dd397b5beed12e3662984cc4afdea2ff6998155b9c74869050d93c | Sha256 | BATLoader Batch File |
| bd62756f0c9a7b1351d95a4f89e4a2703fe3e8b1 | Sha1 | BATLoader Batch File |
| 8eac2855d5a48ec13d6d71a463f40e27 | Md5 | BATLoader Batch File |
| 0e06d91d1d9e7cecc1c2553076fd0df71fc4fe2081b7bd0b6dd25b0ce6b98788 | Sha256 | RedLine Stealer |
| 825c448b5ef5f85e13aae802ca31532f0cf3cae4 | Sha1 | RedLine Stealer |
| ae9ca12bd7d797aa7dc7fe4b8584251f | Md5 | RedLine Stealer |
| e68c2cb879dfb35b9685e966ec0e9f461d2085e67a284888bf2deec93040359c | Sha256 | AMSI Bypass Executable |
| 9f68f5c80fbf35cce6f3a1309ae4ef1acd81f631 | Sha1 | AMSI Bypass Executable |
| 919892434c49fa33abb1fa9eae64355c | Md5 | AMSI Bypass Executable |
Threat Hunting using SIEM queries:
The detection of the “Change PowerShell Policies to an Insecure Level – PowerShell” and “Suspicious Get-WmiObject” rules from the Sigma Integrated Rule Set (SIRS) on GitHub is particularly relevant when dealing with malicious malware. These rules are designed to identify specific behaviors associated with malware infections and potential security risks.
The first rule, “Change PowerShell Policies to an Insecure Level – PowerShell,” focuses on detecting any attempts to modify PowerShell policies in order to establish insecure settings. Malware often targets PowerShell due to its extensive capabilities, allowing threat actors to execute malicious commands or gain unauthorized access. By monitoring for changes to PowerShell policies, organizations can detect and mitigate potential risks, preventing malware from exploiting these vulnerabilities.
Elastic query:
((powershell.file.script_block_text:*Set\-ExecutionPolicy*
AND powershell.file.script_block_text:(*Unrestricted* OR *bypass* OR *RemoteSigned*))
AND (NOT powershell.file.script_block_text:(*\(New\-Object\ System.Net.WebClient\).DownloadString\('https\:\/\/community.chocolatey.org\/install.ps1'\)*
OR *\(New\-Object\ System.Net.WebClient\).DownloadString\('https\:\/\/chocolatey.org\/install.ps1'\)* OR *\\AppData\\Roaming\\Code\\*)))
Splunk:
index=* source="WinEventLog:*"
AND ((ScriptBlockText="*Set-ExecutionPolicy*"
AND (ScriptBlockText="*Unrestricted*" OR ScriptBlockText="*bypass*" OR ScriptBlockText="*RemoteSigned*"))
AND NOT (ScriptBlockText="*(New-Object System.Net.WebClient).DownloadString('https://community.chocolatey.org/install.ps1')*" OR ScriptBlockText="*(New-Object System.Net.WebClient).DownloadString('https://chocolatey.org/install.ps1')*" OR ScriptBlockText="*\\AppData\\Roaming\\Code\\*"))
Microsoft Sentinel Query
Event | where EventLog == 'Microsoft-Windows-PowerShell/Operational' |
where EventID in (4100, 4102, 4103, 4104) |
where ((EventData contains @'Set-ExecutionPolicy' and (EventData contains @'Unrestricted' or EventData contains @'bypass' or EventData contains @'RemoteSigned'))
and not (EventData contains @"(New-Object System.Net.WebClient).DownloadString('https://community.chocolatey.org/install.ps1')"
or EventData contains @"(New-Object System.Net.WebClient).DownloadString('https://chocolatey.org/install.ps1')" or EventData contains @'\AppData\Roaming\Code\'))
The second rule, “Suspicious Get-WmiObject,” is aimed at the management infrastructure used for Windows PCs and servers. Malware can leverage the Get-WmiObject cmdlet to retrieve management information and perform unauthorized activities, such as accessing sensitive data or executing malicious code. Detecting suspicious usage of Get-WmiObject helps organizations identify potential malware activities and prevent further damage or unauthorized access.
By incorporating these rules into a security monitoring system or SIEM, organizations can strengthen their defenses against malicious malware. The collective knowledge and contributions on platforms like GitHub enable organizations to leverage the expertise of the security community and stay ahead of evolving threats. By promptly detecting and responding to malware-related behaviors, organizations can safeguard their systems and protect valuable data from compromise.
Elastic Query:
index=* source="WinEventLog:*"
AND ((ScriptBlockText="*Get-WmiObject*" OR ScriptBlockText="*gwmi*")
AND NOT (Path="*\\CL_Utility.ps1"
AND (ScriptBlockText="*function Get-FreeSpace*")
AND (ScriptBlockText="*SELECT * FROM Win32_LogicalDisk WHERE MediaType=12*")))
Splunk:
index=* source="WinEventLog:*"
AND ((ScriptBlockText="*Get-WmiObject*" OR ScriptBlockText="*gwmi*")
AND NOT (Path="*\\CL_Utility.ps1"
AND (ScriptBlockText="*function Get-FreeSpace*") AND (ScriptBlockText="*SELECT * FROM Win32_LogicalDisk WHERE MediaType=12*")))
Microsoft Sentinel Query:
Event | where EventLog == 'Microsoft-Windows-PowerShell/Operational' |
where EventID in (4100, 4102, 4103, 4104) |
where ((EventData contains @'Get-WmiObject' or EventData contains @'gwmi')
and not (Path endswith @'\CL_Utility.ps1' and (EventData contains @'function Get-FreeSpace') and (EventData contains @'SELECT * FROM Win32_LogicalDisk WHERE MediaType=12')))
Conclusion:
Exploiting the rising popularity of new applications, threat actors (TAs) are capitalizing on the excitement surrounding them. Their primary targets are unsuspecting users who are lured into downloading fraudulent and malicious applications. This trend is especially evident among CapCut users, as TAs relentlessly focus their efforts on targeting them through the deployment of malicious phishing websites. It is essential for users to be aware of these threats and take necessary precautions to protect themselves from falling victim to such deceptive tactics.
Thank you for taking the time to read this blog post. We hope that the information provided has been valuable to you in understanding the importance of detecting and mitigating malicious malware. By staying informed about the latest threats and implementing proactive security measures, you play a crucial role in safeguarding your systems and data. Remember to follow cybersecurity best practices, such as using strong passwords, keeping software up to date, and exercising caution when interacting with unknown or suspicious content. Stay vigilant and stay protected. Thank you again for being a part of our community and for your continued support.