The Akira Ransomware Saga: Origins, Tactics, and Countermeasures
In the ever-evolving landscape of cybersecurity threats, one name has recently gained notoriety – Akira Ransomware. This malicious software has wreaked havoc […]
Read MoreCopyright 2023 by EventLogs!!
In the ever-evolving landscape of cybersecurity threats, one name has recently gained notoriety – Akira Ransomware. This malicious software has wreaked havoc […]
Read More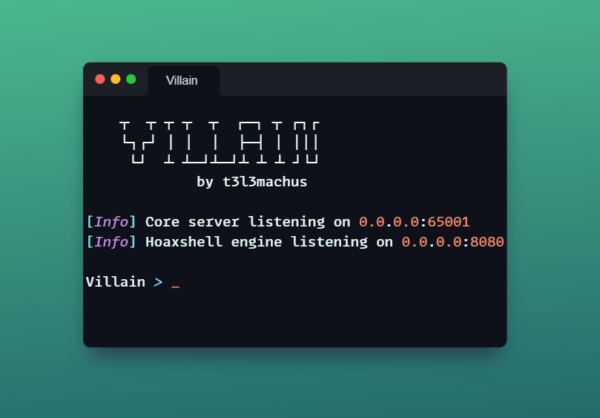
Hey there, security lovers! Do you like hacking stuff and breaking into networks? Do you enjoy playing with C2 frameworks and reverse […]
Read More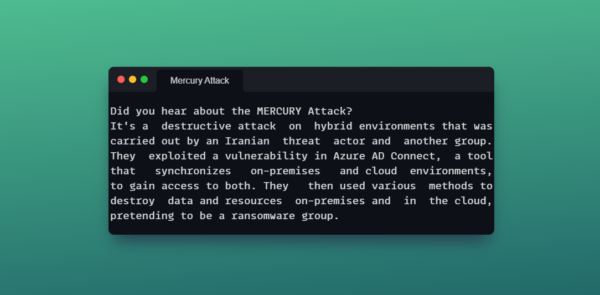
The article written by Paul Robichaux for Practical365.com describes a new attack that exploits Azure AD Connect to compromise both on-premises and […]
Read MoreIn recent years, cyber attacks have become increasingly sophisticated, and one of the most dangerous types of attacks that organizations face is […]
Read More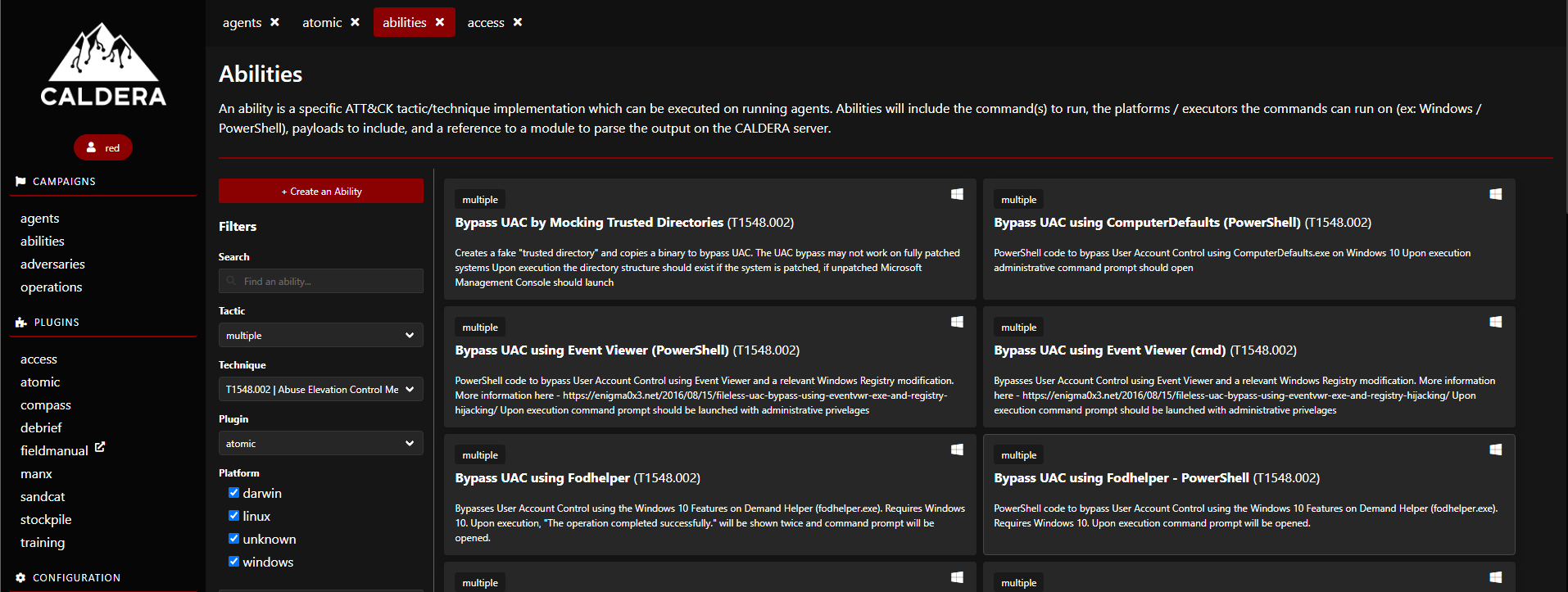
This article demonstrates a framework for conducting red team activity using open-source breach & emulation. In addition to MITRE simulation, it also […]
Read More
NTLM hashing is a technique used to authenticate a user’s password to a Windows service. This method uses the hash of the […]
Read More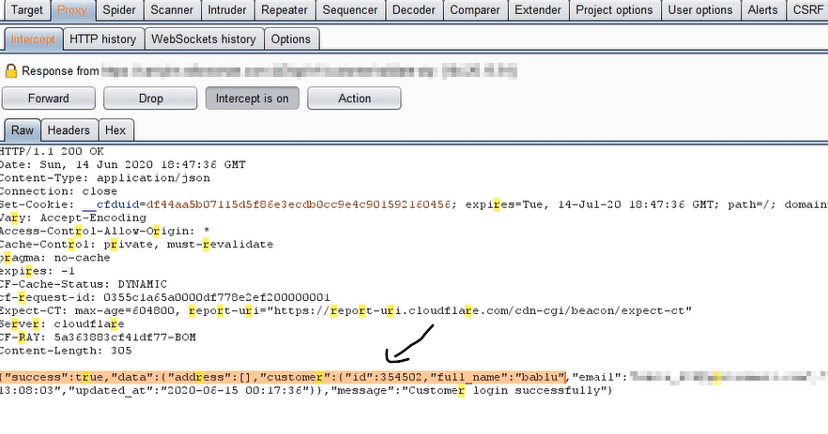
A bug bounty program is a great way to get valuable feedback and even earn some money. It’s a perfect opportunity to […]
Read More
As I was working on a pentest report recently, I noticed that there were a few common wins for pentesters that came […]
Read More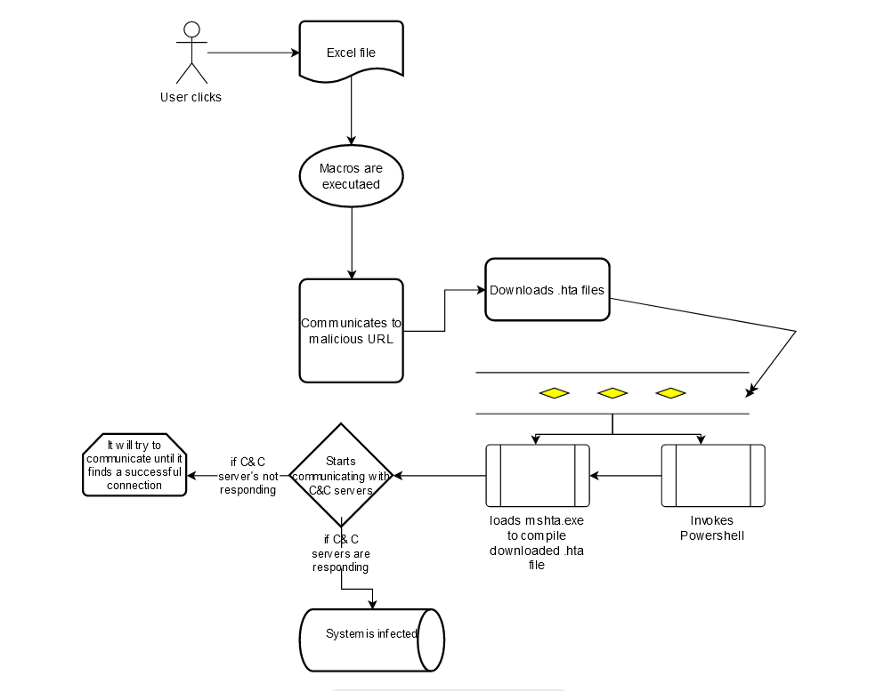
Hello everyone, I hope you are doing well. I’m back with a useful article about “Emotet — Trojan” and what happens when […]
Read More