My First Bug-Bounty
A bug bounty program is a great way to get valuable feedback and even earn some money. It’s a perfect opportunity to learn more about the product you’re building or service you’re providing. Here are some tips on how I found & what I learned about bug bounties.
Introduction:
My name is Sai Prashanth. A SOC Engineer , Security Researcher and Part time Bug bounty hunter. I work as a Senior SOC Engineer at ECI (Eze Castle Integrations) where I love to solve real world problems using Blue Team tools and techniques.
It all started a few years ago and I just thought of writing this article because this bug can easily be detected in multiple area’s.
There was a shopping website and while performing a recon, I have found a vulnerability in their website. As a result, anyone can log in into someone else’s account and change the data, collect information like mobile no address or modify the order details like delivery address etc.
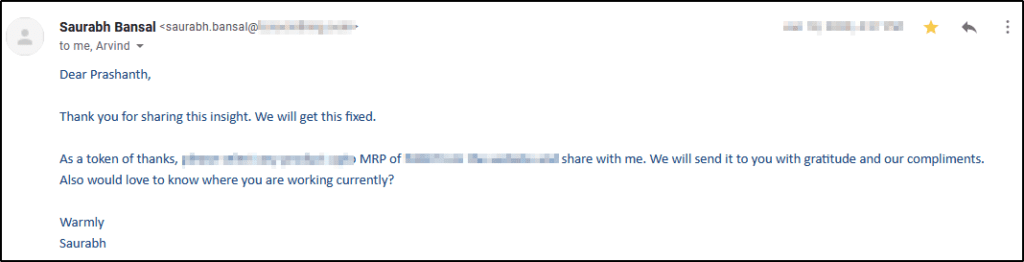
What’s the bug now?
As part of performing recon on one of the website’s login pages, I have created a user account and then intercepted the traffic via BurpSuite and could see that a unique user ID had been assigned for me. In addition, I modified the user’s ID with a random ID, which gave us access to other users’ orders, addresses, mobile numbers, as well as setting a new email / mobile number, which gave me full control of the account. This process is ideally called as IDOR.
What is an IDOR vulnerability?
Insecure Direct Object References (IDOR) occur when an application provides direct access to objects based on user-supplied input. As a result of this vulnerability attackers can bypass authorization and access resources in the system directly, for example database records or files.
There can be many variables in the application such as “id”, “pid”, “uid”. Although these values are often seen as HTTP parameters, they can be found in headers and cookies. The attacker can access, edit or delete any of other users’ objects by changing the values. This vulnerability is called IDOR.
First, it needs to understand the application flow developed by software developers. All the module functions and their sub-modules functions need to be understood when the logged-in user into the web/mobile application. It is also important to remember that this vulnerability is as severe as XSS, CSRF in security testing and as a type of vulnerability that is not easily discovered (automatized testing or manual testing).
Proof of Concept:
My user ID:
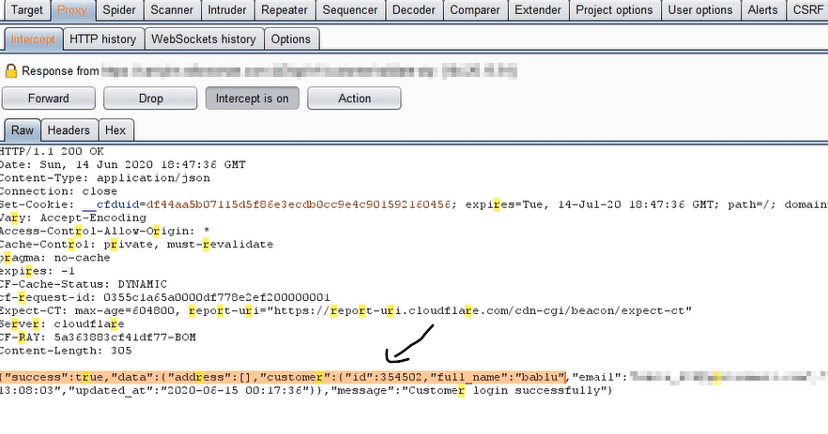
User ID modified via Burp:

As soon as we update the user ID, and forward the request using burpsuite, we have access to some other user’s profile.

Due to privacy policies, I do not disclose URLs and internal data, but I believe it’s enough to understand bugs.
Tools :
Reference :
https://portswigger.net/web-security/access-control/idor
https://hackerone.com/reports/227522
https://hackerone.com/reports/751577
I appreciate you reading this blog. If you think it has been valuable, please give it a thumbs up.If you enjoy it, share with your friends and other members of your community. Stay tuned for the next blog!