Red Teaming with Caldera (Attack and Detect)
This article demonstrates a framework for conducting red team activity using open-source breach & emulation. In addition to MITRE simulation, it also features a number of other functions that can be incorporated into the simulation process.
We’ll start with Caldera as an attack strategy and Elastic as a detection strategy:-)
Caldera
Caldera is a breach and adversary emulation tool that provides a simple way to automate adversary emulation, assist manual red-teams, and automate the incident response process.
The framework consists of two components:
In this repository, you will find the framework code, which is the code that makes up the core of the system. In addition, we have included an asynchronous command-and-control (C2) server with a REST API and a web interface to interact with it.
There are two types of plugins: Extensions and Plugins. Extensions are repositories that expand the capabilities of the core framework and add new features. The types of agents, the type of reporting, the type of TTP collections is just some of the examples.
Pre-requisite & dependencies
These requirements are for the computer running the core framework:
- Any Linux or MacOS
- Python 3.7+ (with Pip3)
- Recommended hardware to run on is 8GB+ RAM and 2+ CPUs
- Recommended: GoLang 1.17+ to dynamically compile GoLang-based agents.
Source: https://github.com/mitre/caldera
I’ve already setup the Lab and the documentation is already available here.
Campaigns
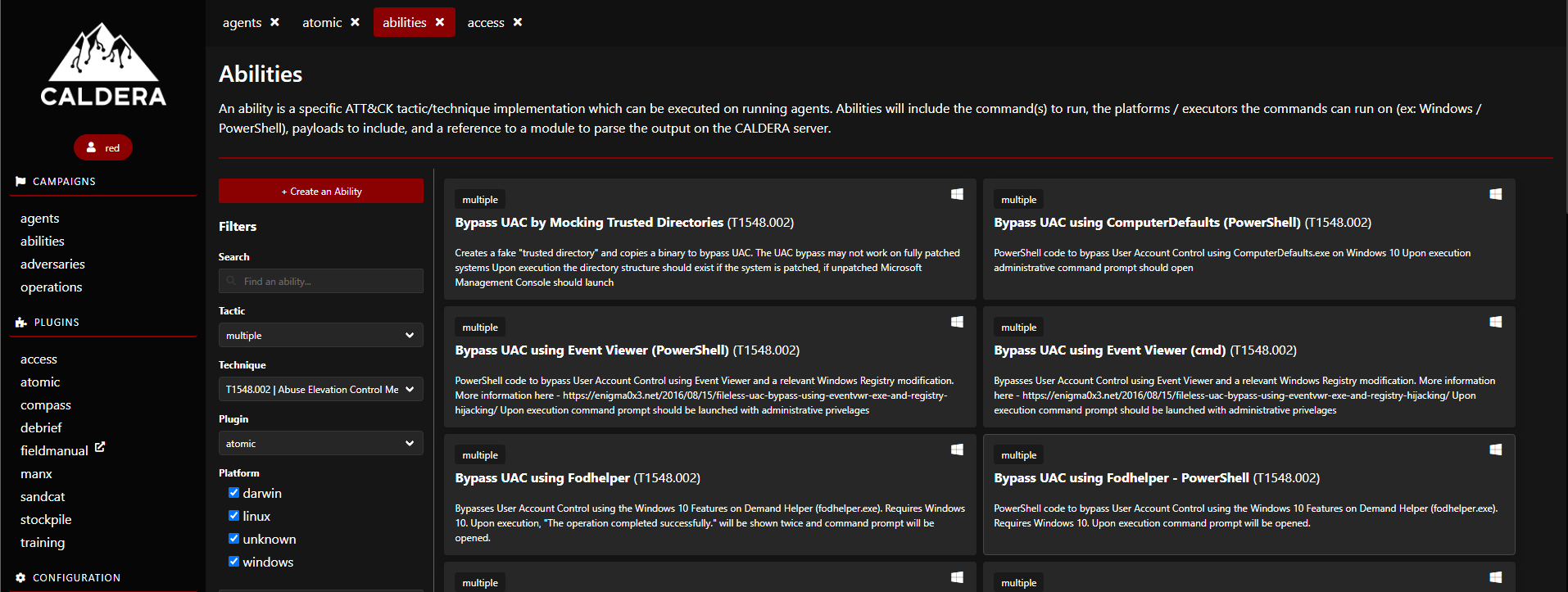
There are several agents, adversaries, and operations that fall under the Campaigns category, which may be used to build up the numerous agents, adversaries, and operations you will need for a red team operation or adversary simulation to take place.
After installing Caldera, the first step is to deploy the agent :
Step1: Deploy an Agents
First, we need to implant an agent inside the target system in order to gain access to it for the first time.
The following steps should be followed in order to set up an agent or listener:
If you click on the agent’s tab on the campaign tab, you will see the following: (I’ve already setup agents )
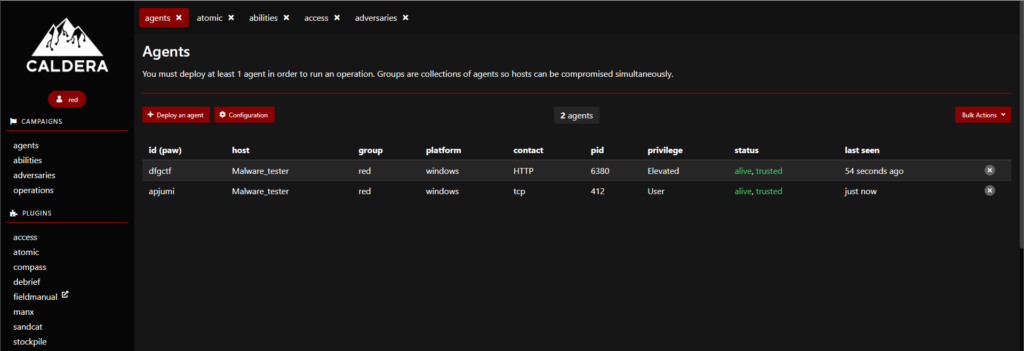
Under our abilities tab, we have the complete MITRE Framework including their procedures as well as other information.
Step2: Abilities
An ability is a specific ATT&CK tactic or technique implementation that can be implemented on a running agent in order to execute the tactic or technique. CALDERA’s capabilities will include a command or commands to run, a platform or executor to run them on (e.g. Windows/PowerShell), payloads to include, and a reference to a module that will parse the output on the CALDERA server once the command is executed.
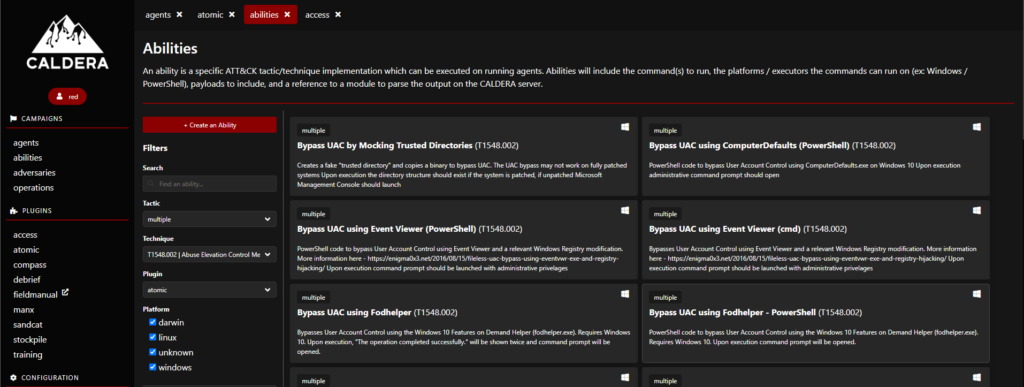
In the above SS, as you can see, we are able to select the Platform and the related TTP. It is prudent to take a discovery as a tactic & Linux as a platform (the same tactic that was demonstrated in this article for Windows)
When we navigate to the Access Tab, we can actually select a specific Ability and choose a custom Tactic, a Technique or an Ability that will be run on the victim’s machine after selecting an Ability as shown below:
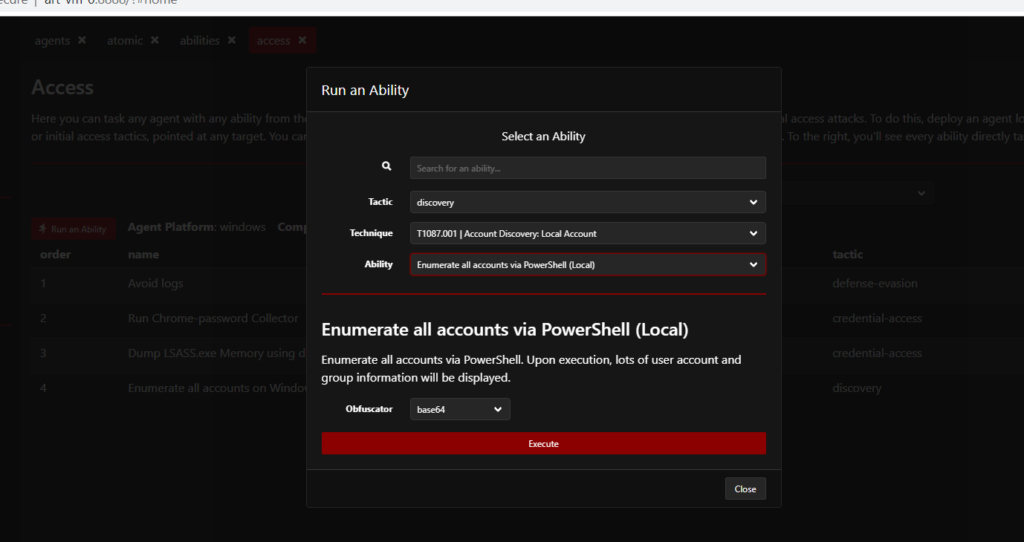
It begins to run commands on the agent that has been deployed at the beginning of the process, after you click the Execute Tab

There is another advantage of Caldera, that it also responds back with the output of the attack along with the logs of the agents, if the attack is successful or not.
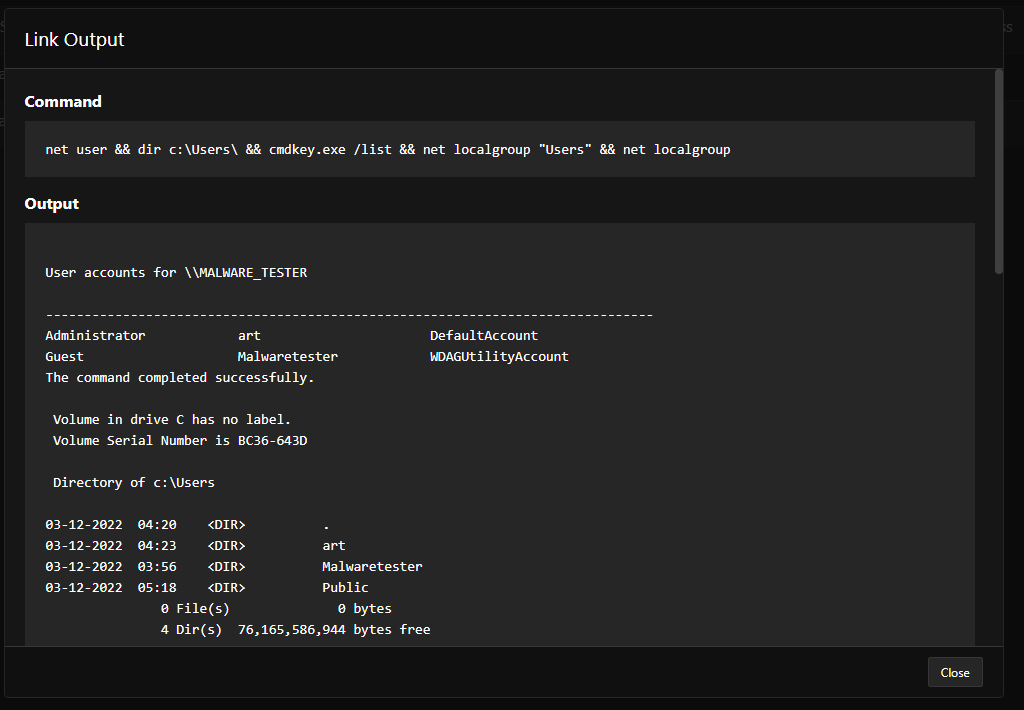
Here’s a look at whether our SIEM has captured these events or not.


One of the unexpected things I discovered was that when I was executing a malicious PowerShell script, Total AV was not able to capture the malicious c2c communications.
I appreciate you reading this blog. If you think it has been valuable, please give it a thumbs up. If you enjoy it, share with your friends and other members of your community. Stay tuned for the next blog!